Counterfeiting is on the rise and shows no signs of slowing down. It’s a big problem with a big price tag. How big? According to Robert Handfield, a professor of supply chain management at North Carolina State University, back in the 1980s, counterfeit products were a $30 billion trade problem. Today counterfeit products exceed more than $600 billion in trade.
Also, according to the Document Security Alliance (DSA): “The average organization loses 10% of revenue from counterfeiting, and it has been estimated that the value of counterfeit goods globally exceeds 1.7 trillion dollars annually”. In addition to counterfeit goods, counterfeit documents are a huge problem that extends beyond financial loss. “Governments are seeing more sophisticated counterfeits and fraudulent use of their issued documents—travel documents, identity documents, and currency. In turn, counterfeit and fraudulent documents can be used to obtain legitimately issued documents.”
Although it is impossible to completely eliminate the possibility of counterfeiting, you can make it difficult enough that it’s not worth the effort for criminals. One of the most cost-effective ways you can protect documents or products from counterfeiting is by using fluorescent pigments and dyes as part of a layered security approach.
In today’s blog, we are going to explain what a layered security approach is and how fluorescent pigments and dyes can play a role in protecting document security and product authenticity in a cost-effective manner.
Jump to:
What is a layered security approach?
A layered security approach is pretty much what it sounds like … using or combining multiple methods to prevent fraud or a security breach. This concept is applied by different industries, technologies, and commodities to increase security effectiveness. However, for the purpose of this article, we are going to focus on documents and products.
When it comes to document and product security, there are many different elements that can be used to create a layered approach. Security elements include but are not limited to:
- Security Inks: invisible fluorescent ink, luminescent taggants, infrared inks
- Luminescent security threads and fibers
- Color Shifting Inks (OVI’s)
- Holograms, photopolymer films
- Tamper Evident labels
- Watermarks
- Micro text
- Intaglio, embossed/raised printing
- Software/Database cloud solutions such as 2D code verification via smartphone apps
All of these elements and methods fall into 2 main categories: Overt and Covert security features.
In a layered security approach, multiple features are applied or combined in the document or product. These features can be either overt, covert, or a combination of both.
What are Overt and Covert security features?

Overt security features
Overt security features are visible to the naked eye under normal lighting conditions. For example, the color-shifting ink on a 10-dollar bill, an embedded security thread, or a properly embedded watermark. Overt features also include tactile features that can be felt by touching the item, such as embossed areas (raised ridges from Intaglio printing).

Covert security features
Covert security features are not visible to the naked eye and usually require some level of training and/or knowledge of the security feature. Detecting these features often requires additional tools or equipment. These range from readily available tools such as a UV Light source or magnifying lenses to forensic analytical instruments such as spectrophotometers. Examples include invisible marks or codes printed with UV fluorescent inks and hidden text or images embedded in the document.
A visualization of a layered security approach
There are many ways to create a layered security approach. The $100 bill is a great example of a layered security approach as it relates to currency. The $100 bill has many security features, both overt and covert. Some covert features in U.S. currency are not advertised in the brochures and/or made public knowledge.
Examples of security features used on the $100 bill include (but are not limited to):
Overt
- watermarks
- specific paper composition
- color-shifting inks
- 3D security ribbons
Covert
- UV fluorescent & IR (infrared) inks, threads and polymers
- microtext, hidden text/images
- magnetic ink
- forensic features (custom designed materials & techniques requiring lab equipment)
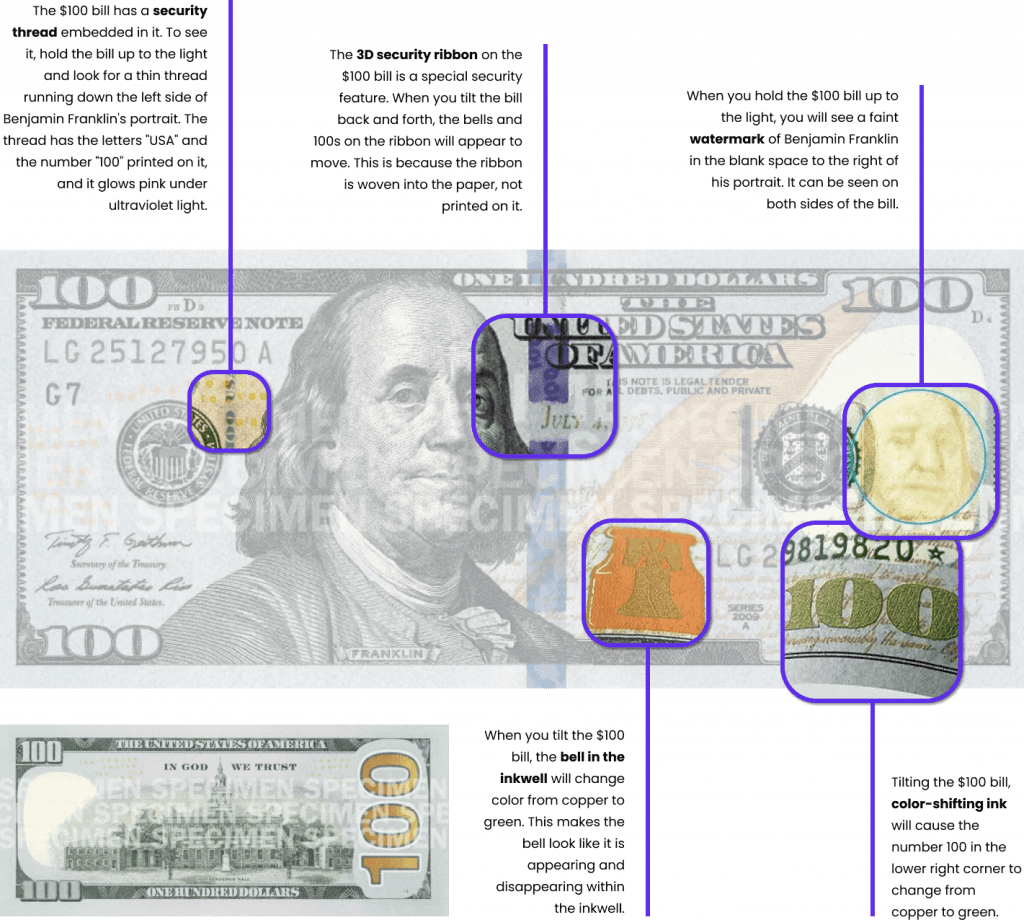
Image credit and citation: www.uscurrency.gov/denominations/100
What is “track and trace” technology? Is it used for product authentication and security?
The primary purpose of track and trace systems is to locate and monitor past and present locations of shipments, inventory, and products throughout an entire supply chain and are outside the scope of this article. Track and trace methods include barcodes, RFID chips, and other database-driven technologies. Some track and trace methods do provide levels of counterfeit protection and/or can be integrated with layered security features.
Pharmaceutical track and trace
One common use of track and trace systems is in the pharmaceutical industry. Pharmaceutical track and trace is a system that uses records, systems, and processes to track and trace pharmaceutical products from the manufacturing plant to the pharmacy shelf. This system is critical for ensuring the safe and effective distribution of pharmaceutical products to consumers.
Here are some of the key benefits of pharmaceutical track and trace:
- It can help to prevent counterfeit and falsified medicines from entering the supply chain.
- It can help to identify and recall contaminated or defective products quickly and efficiently.
- It can help to improve the efficiency of the pharmaceutical supply chain.
- It can help to improve patient safety.
What is the “most” secure type of security feature?
Many experts define three levels of security features:
The “most secure” (and expensive) methods are not always the best or most effective solution. We believe the best solution for document security and product authentication are cost-effective methods suitable to your application that are hard to replicate but easy to validate.
We believe that a combination of “lower level” security features applied in a skillful manner can actually raise the level of security and protection while keeping costs down and the complexity of implementation at a reasonable level. The result is a cost-effective security solution that is greater than the sum of its parts. Further, some security features can function as a decoy to suggest a lower level of security while hiding another invisible feature.
Why a layered security approach is important
As we previously mentioned, counterfeiting and fraud is on the rise and is a costly problem. But there are reasons beyond the financial cost of counterfeits and fraud, including protecting your brand, protecting against fraud, and health and safety risks
Protecting your brand
One reason a layered security approach is important is that it can help protect your brand. We’ve all seen what happens when a product is compromised and a brand’s reputation is negatively affected.
Counterfeit high-end hair care products often show up on the market. If you’ve ever bought Paul Mitchell products from a grocery store or drug store, you’ve probably bought a counterfeit product. Since counterfeit products often are diluted, expired, or fake, the quality of the product is subpar. The results? If this happens enough, the Paul Mitchell brand is going to take a hit.
Brand protection methods employ any of the security features mentioned above and usually a combination of the above. Often overt and covert features are combined.
For example, a track and trace method can be combined with a fluorescent security mark, with each being independently verifiable. Conversely, layered security features may be integrated together, such as a fluorescent mark or code combined with a completely invisible infra-red (IR) element
Health and safety risks
Other problems that can be prevented with a layered security approach include health and safety risks. According to the Department of Homeland Security, “the production and trafficking of counterfeit goods poses a significant health and safety threat to consumers. It also impacts the economic growth of legitimate businesses and consumers through lost revenue, downtime, and replacement costs.”
The Most Dangerous Counterfeit Products:
- Automotive parts
- Electronics
- Prescription drugs
- Cosmetics
One example of how dangerous counterfeit products can be is the opioid crisis. The CDC said fake prescription pills accounted for nearly 5% of deaths over the period studied, although that rose to nearly 15% in the western US. The agency said demand for fake opioid painkillers was highest in the west of the US, while half of deaths in the south were from counterfeit versions of the Xanax.
How UV inks and taggants can be applied to create a layered security approach
There are many different elements that can be part of a layered security approach. Angstrom Technologies, Inc., specializes in UV inks and taggants. UV inks and taggants play a vital role in preventing counterfeiting and fraud, and they are an effective and affordable option for a layered security approach.
Fluorescent Inks and Taggants lend themselves especially well to combining with other features to create a robust security solution.
One effective technique is to use a “standard” fluorescent mark as a decoy for another completely invisible feature. For example, a counterfeiter can see a common fluorescent mark with a cheap black light and copy it, thinking that this is the extent of the security mark. The counterfeit will fail upon inspection because the other more hidden material is not present.
Another effective technique is bi-fluorescent ink, using material that fluoresces a different color depending upon the wavelength of UV light used to examine it.
Why UV inks and taggants are a smart choice for a layered security approach
There are many reasons why UV inks and taggants are excellent options to use in a layered security approach. UV inks and taggants are:
- Cost-effective
- Versatile—combines well with other features and technologies
- Flexible—works in many types of media, inks, plastic, etc.
- Proven effective with a long track record
- Wide application across many industries
Examples of how UV inks and taggants are used in a layered security approach
To help put some of what we’ve discussed in context, we provided a list of examples of how UV inks and taggants are used in a layered security approach.
Special polymer threads of a specific width are embedded and placed at a specific location in the substrate. They are micro-printed with a specified text. Finally, the threads contain a fluorescent adhesive that fluoresces a specific color that confirms the denomination. All three elements indicate authenticity: size/ location, print text, and fluorescent color
A proprietary barcode is applied to the document in addition to a stamped design that contains a fluorescent material. Two devices independently verify the authenticity of the document.
A fluorescent mark is combined with another security ink that is only detectable with a specific device. Both the fluorescent ink and the enhanced security ink must be detected at the same time to be verified.
The printed mark fluoresces a different color when exposed to shortwave UV or longwave UV. Marks can be two different inks in different locations in the article or integrated into a single ink for a single mark.
A fluorescent material is designed with a specific spectrophotometric profile that is verifiable based on the spectral analysis. For example, a material that appears to fluoresce white actually comprises several fluorescent emission peaks of various wavelengths and amplitudes in a specific combination. This creates a unique profile that is only verifiable via spectral analysis.
Protect your brand and products with a layered security approach
Don’t wait until your products are compromised. Protect your brand now with a layered security approach. We specialize in cost-efficient security solutions that can be customized to your product’s specific needs. Fill out the form below to get started, and one of our representatives will get back to you shortly.
Angstrom Technologies Inc. Are the Experts
Angstrom Technologies Inc. specializes in the development, custom formulation, and manufacture of invisible fluorescent pigments and dyes to exact specifications for specialized applications that require integration with a wide variety of materials such as inks, varnishes, plastics, and adhesives. Our products are designed for numerous industries and are excellent choices for document security, process control, and other applications. If you’re interested in learning how we can help, reach out to us today.